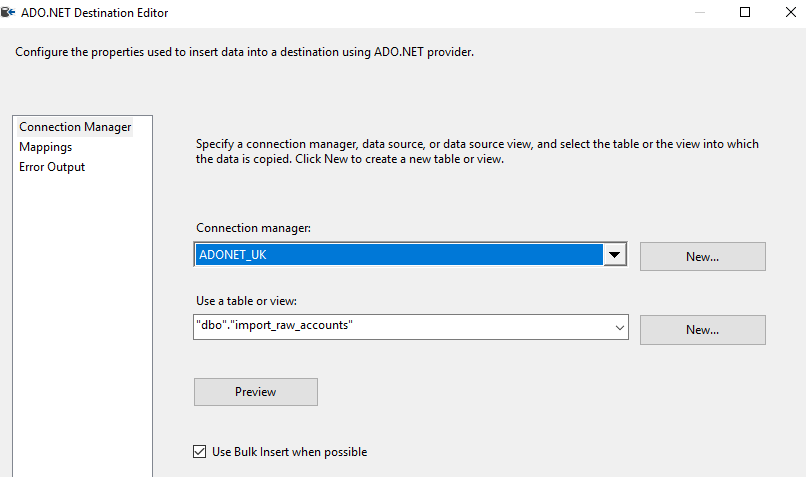
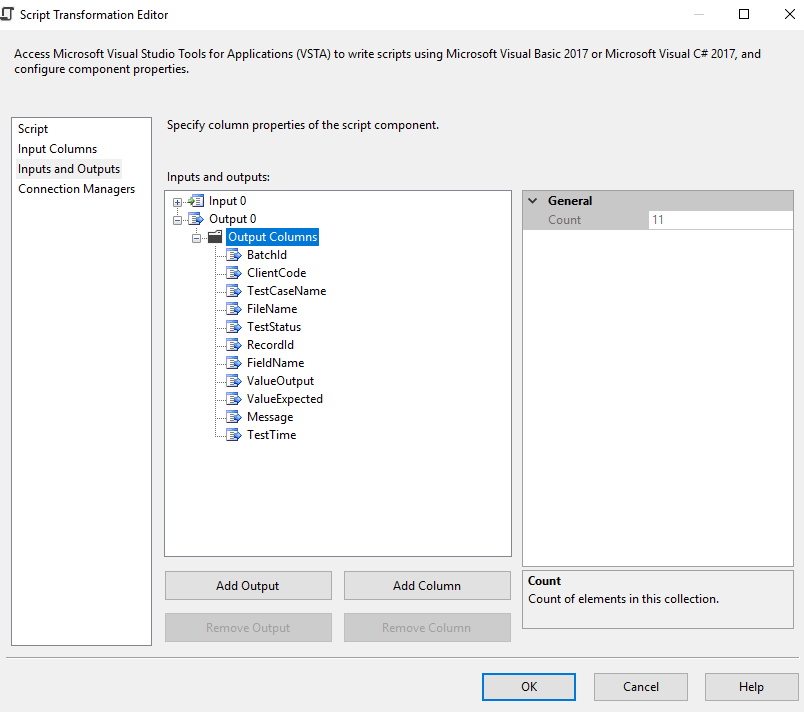
This week I have been having trouble connecting to my Azure server via RDP. I keep getting below errors:
-The number of connections to this computer is limited and all connections are in use right now.
I can connect to server if I changed inbound security rule to allowed my IP address only. But I cannot use white IP list inbound rule as I don’t have static IP.
Then I did some deep investigation and try to tracking failed logon information from system event.
I checked Event Viewer -> Windows Logs -> Security there are lots of Audit Failure event looks like below:
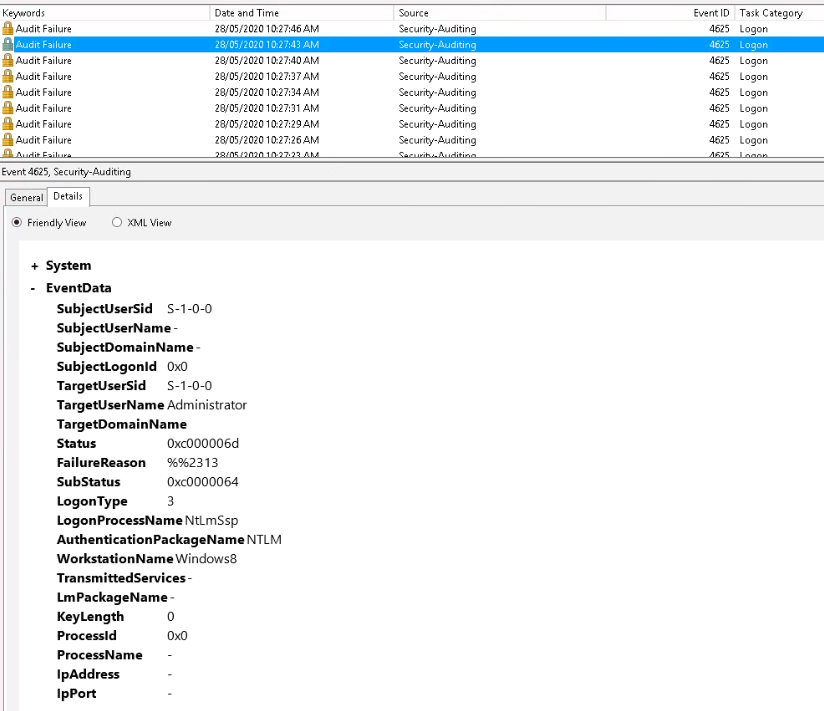
But as you see, it is completely useless. I only can guess their are some attackers tried to logon with a username of Administrator and the Logon Type is set to 3 (generic network logon), and there is no Source Network Address recorded.
But in Event Viewer -> Applications and Services Logs -> Microsoft -> Windows -> RemoteDesktopServices-RDPCoreTS I found lots of below warnings:
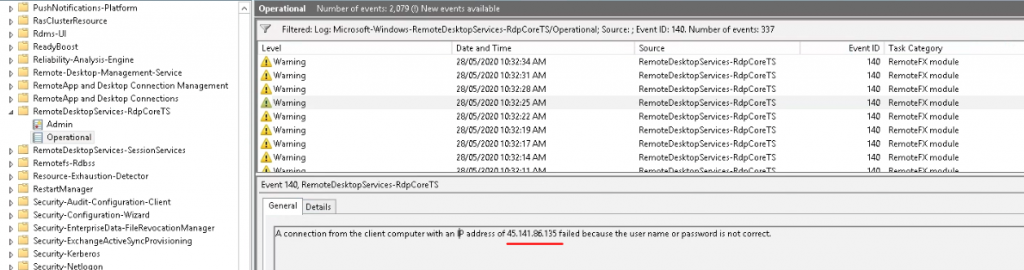
In Windows Server 2012 and later version, if an attacker attempts to logon but fails to do so AND uses a username that DOES NOT EXIST on the targeted RDS host or domain that the host is a member of, Event ID 140 is logged, showing you the source IP of the attacker.
I added this IP to Azure blocked IP list then issue is fixed.